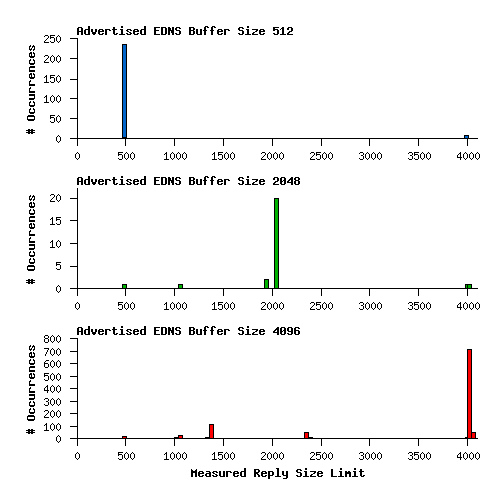
Over on the IETF namedroppers mailing list there is a discussion about DNSSEC and UDP fragmentation. See this thread, for example. Since the OARC Reply Size Test has been going for a couple of months now, I thought maybe it would have enough data for a decent analysis. Here's what I found: