30 Sep 2020 UPDATE: OARC's ODVR service has now been removed from service and shut down
4 April 2018 UPDATE: The ODVR BIND servers has been modified to REFUSE any queries without using DNSSEC!
20 May 2016 UPDATE: ODVR DNS servers have renumbered! This page has been updated to reflect changes as appropriate.
7 June 2011 UPDATE: The .de zone is now fully signed and the corresponding DS Resource Record has been added to the root zone, so the testbed redirection has been removed from both resolvers.
4 October 2010 UPDATE: We have now added the .de DNSSEC Testbed to both resolvers.
How To Use ODVR
OARC is pleased to offer dual-stack (as in IPv4 and IPv6), open DNSSEC-validating resolvers ("ODVR") that anyone can use to experiment with DNSSEC. The IP addresses for ODVR nameservers are:
| Instance | IPv4 | IPv6 | ||
|---|---|---|---|---|
| BIND 9 | 184.105.193.73 | 2620:ff:c000:0:1::64:20 | ||
| Unbound | 184.105.193.74 | 2620:ff:c000:0:1::64:21 |
You might like to manually query the ODVR nameservers with a tool such as dig. Be sure to add the +dnssec option:
$ dig +dnssec @184.105.193.73 iis.se
The AD bit in the response flags tells you that the reply data has been validated:
;; flags: qr rd ra ad; ...
Another way to use ODVR is to place the following lines in your Unix /etc/resolv.conf file:
nameserver 184.105.193.73 nameserver 184.105.193.74
Windows users can manually set DNS servers in the Internet Protocol Properties dialog of a network connection.
Finally, the client (such as dig) that you use to test against ODVR should allow you to use this tool by specifying IPv4 or IPv6 options.
Trust Anchors
ODVR has been configured to automatically update its list of trust anchors including that at the root zone.
Data Collection
OARC collects data from the ODVR nameservers and makes this data available to our members for research purposes.
Traffic Graphs
These graphs, updated nightly, show the number of queries received with and without the "DO" bit set, and the number of responses sent with and without the "AD" bit set.
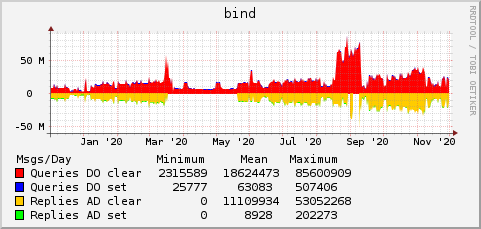
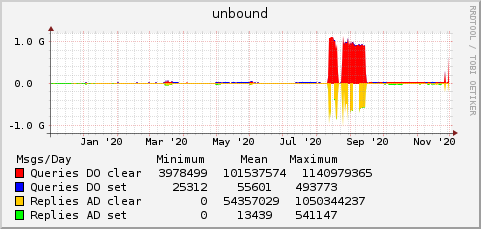
Configuration Files
BIND: UNBOUND:Frequently Anticipated Questions
Q: Does it mean all my DNS lookups are secure if I use OARC's validating resolvers?
A: No, probably not, for the following reasons:
- Most zones are not yet signed. Chances are that, for most of your DNS queries, there will not be any DNSSEC signatures. However, we expect this to improve over time as more and more zones take advantage of DNSSEC.
- Most end-user applications (think Web browser) and stub resolvers (a part your computer's operating system) do not yet perform DNSSEC validation. This means that the channel between you and the OARC nameserver is still vulnerable to attack. In other words, security of the DNSSEC transaction is only guaranteed up to the point where the validation has been performed.
Q: Then why are you doing this?
A: A few reasons:
- So that you can play with DNSSEC without changing the configuration of your own nameserver.
- To convince you that a DNSSEC-validating resolver works almost exactly like a non-validating resolver and that you should go ahead and enable DNSSEC on your own resolvers.
- To collect and publish data on adoption of DNSSEC over time.
Q: Can I use ODVR nameservers provide protection from Kaminsky-style spoofing attacks?
A: The answer is complicated and depends on a number of other factors. Generally, this should not be your motivation for using ODVR. If you are stuck using a DNS resolver with poor source port randomization then ODVR may make you more secure. However, a determined attacker could probably spoof answers that appear to come from the ODVR nameservers and give you bad answers.
Q: What is OARC's Privacy Policy for use of ODVR nameservers?
A: In line with OARC's mission, query data from our various testbed resolvers is logged and stored for non-commercial, public benefit research purposes. Users of the service should be aware this may include personally identifiable information. OARC has strict policies and processes in place, set out in the DNS-OARC Data Sharing Agreement to limit access to this data to bona-fide OARC Members and researcher Participants.
Q: I thought open resolvers were a bad thing?
A: It's true that open resolvers are usually considered to be a problem and have been used — in combination with source address spoofing — to conduct large-scale DDoS attacks. Such attacks are made possible because (1) there are hundreds of thousands, if not millions, of open resolvers, and (2) their owners/operators are unaware of the openness. The ODVR nameservers are rate-limited and closely monitored. If we have reason to suspect abuse of the ODVR nameservers, we will act quickly to stop it. Please contact the OARC Admin if you have abuse concerns.
Q: Can DNS-OARC members have non-rate-limited access?
A: Absolutely. Write to the OARC Admin to find out how.
